Insider threats are a significant concern for organizations of all sizes. They can cause severe damage to an organization’s reputation, finances, and operations. To mitigate these threats, many organizations develop insider threat programs. These programs provide a framework for identifying, detecting, and responding to insider threats.
Insider threat program plans are an essential part of an effective insider threat program. They provide a roadmap for how an organization will address insider threats.
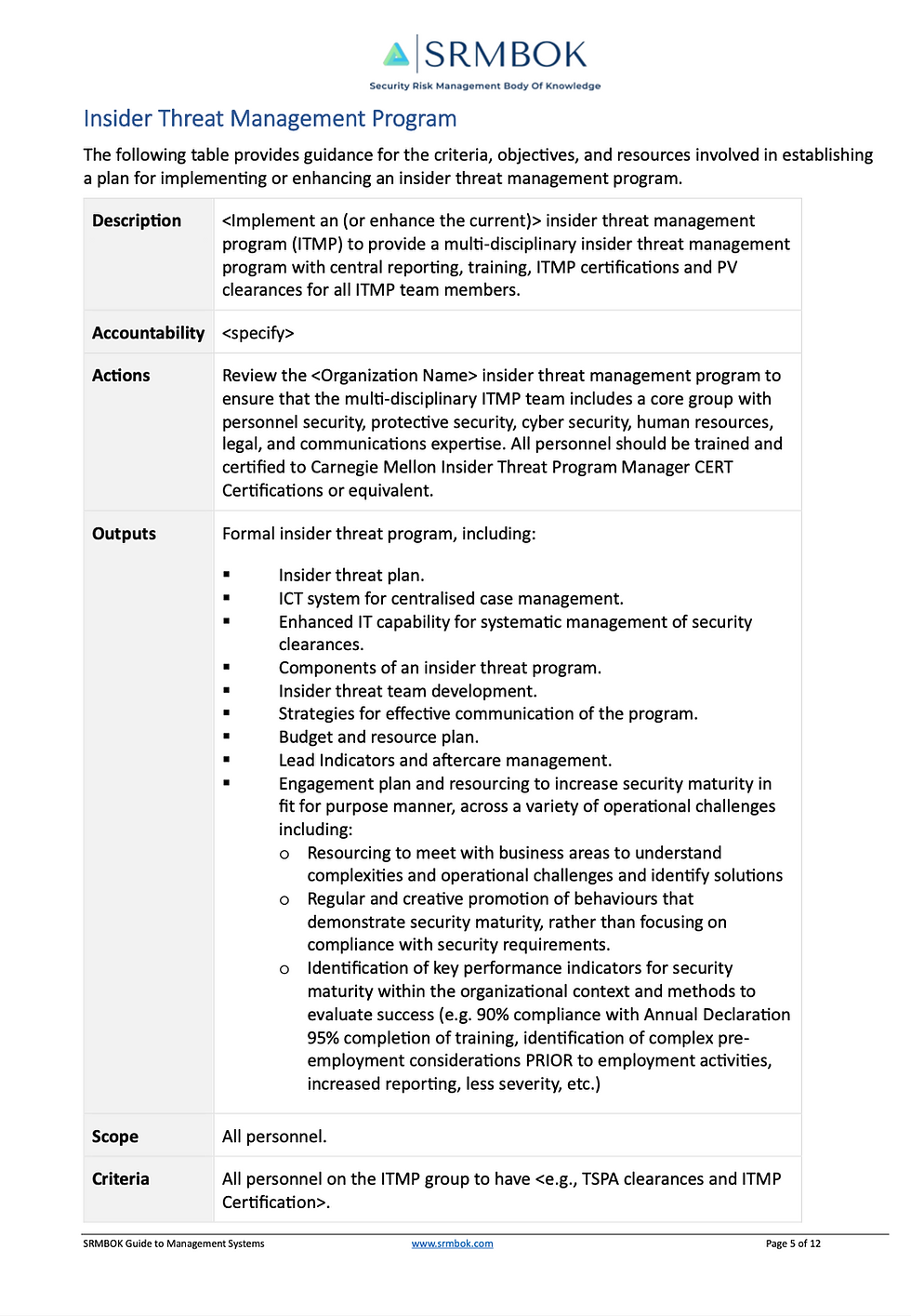
Developing an Insider Threat Program Plan
Developing an insider threat program plan is a complex process that requires input from multiple stakeholders across the organization. The following steps can help you develop an effective insider threat program plan:
1. Define the scope of the program. The scope of the program should include the types of insider threats that the program will address, the assets that are to be protected, and the roles and responsibilities of the various stakeholders involved in the program.
2. Conduct a risk assessment. A risk assessment should be conducted to identify the potential insider threats that the organization faces. The risk assessment should consider the organization’s size, industry, and operations.
3. Develop a response plan. The response plan should outline the steps that the organization will take to respond to an insider threat. The response plan should include procedures for investigating insider threats, mitigating the damage caused by insider threats, and prosecuting insider threat actors.
Essential Elements of an Insider Threat Program Plan
There are several essential elements that should be included in an insider threat program plan. These elements include:
1. Definition of insider threat. The plan should define what constitutes an insider threat. The definition should be broad enough to encompass all potential insider threats, but it should also be specific enough to provide guidance to employees on what behaviors are prohibited.
2. Risk assessment. The plan should include a risk assessment that identifies the potential insider threats that the organization faces. The risk assessment should consider the organization’s size, industry, and operations.
3. Prevention measures. The plan should include a list of measures that the organization will take to prevent insider threats. These measures should include both technical and non-technical controls.
4. Detection measures. The plan should include a list of measures that the organization will take to detect insider threats. These measures should include both automated and manual controls.
5. Response measures. The plan should include a list of measures that the organization will take to respond to insider threats. These measures should include procedures for investigating insider threats, mitigating the damage caused by insider threats, and prosecuting insider threat actors.
Once an organization has developed an insider threat program plan, it is essential to implement the plan and regularly review and update it. By following these steps, organizations can help mitigate the risks posed by insider threats.